Bacon's Cipher Simulator
Explore the secrets of Bacon’s Cipher and experiment with encoding and decoding messages using this classical substitution technique with our interactive simulator.
Bacon's Cipher
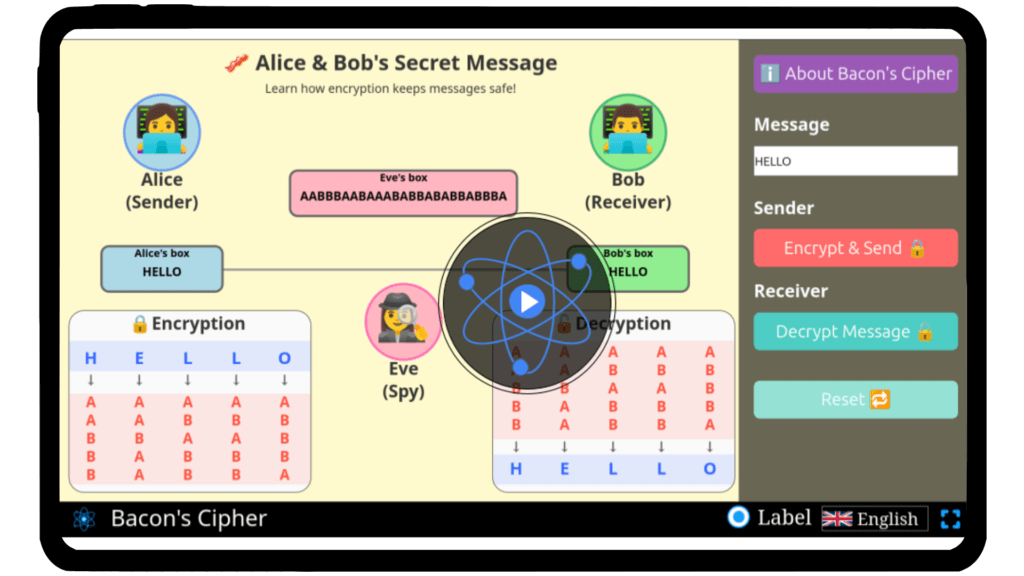
Language and secrecy surround us, shaping communication in subtle ways. Have you ever wondered how hidden messages can be encoded in plain sight? Bacon’s Cipher, a classical method of steganography, transforms letters into patterns of A’s and B’s, concealing the true message beneath a simple text. With our interactive simulator, you can explore this historic cipher hands-on. Encode your own secret messages, decode hidden texts, and uncover the clever logic behind this ingenious technique. Begin your journey into the world of secret writing — experiment with Bacon’s Cipher today!
Mathematical description
Bacon’s Cipher is a binary-based steganographic substitution system.
Each letter of the alphabet is encoded as a 5-bit binary pattern, represented using two symbols — traditionally A and B.
Encoding Principle
Each plaintext letter P is mapped to a fixed 5-bit binary sequence:
P→b1b2b3b4b5,bi∈{A,B}
A corresponds to 0
B corresponds to 1
Thus, each letter of the alphabet becomes one of the 32 possible 5-bit combinations.
Example
Plaintext:
HELLO
Using the classical Baconian mapping:
H → AABBB
E → AABAA
L → ABABA
L → ABABA
O → ABBAB
Ciphertext (A/B pattern)
AABBB AABAA ABABA ABABA ABBAB
This 5-bit pattern can then be hidden using any binary distinction such as:
uppercase / lowercase
bold / unbold
two different fonts
two colors
symbols like 0/1 or X/O
FAQs on Bacon's Cipher
Qus 1. What is Bacon’s Cipher?
Bacon’s Cipher is a method of steganography invented by Francis Bacon in the early 17th century. It encodes messages using a series of two different symbols (commonly A and B) to represent each letter of the alphabet.
Qus 2. How does Bacon’s Cipher work?
Each letter of the plaintext is replaced with a 5-character combination of two symbols (A and B). For example, “A” might be “AAAAA” and “B” as “AAAAB.” By grouping letters in blocks of five, messages can be hidden in seemingly ordinary text.
Qus 3. What is the principle behind Bacon’s Cipher?
The principle is steganography, hiding the existence of the message itself rather than making it unreadable. Variations in fonts, letter styles, or formatting can encode the binary-like A/B patterns.
Qus 4. Where was Bacon’s Cipher historically used?
Francis Bacon proposed this cipher in 1605 as a method for secret communication. It was primarily used for intellectual exercises or to convey hidden messages in letters and manuscripts.
Qus 5. How is Bacon’s Cipher applied today?
Modern applications include educational tools to teach binary encoding, puzzles, games, and digital steganography, where the A/B patterns can be hidden in images, text formatting, or HTML/CSS.
Qus 6. Can Bacon’s Cipher be broken easily?
Since it’s a substitution-based cipher with a fixed binary encoding, it can be broken with pattern recognition if the existence of a hidden message is suspected. However, its strength lies in hiding the fact that a message exists.
Qus 7. What’s the difference between Bacon’s Cipher and other ciphers like Caesar or Vigenère?
Unlike classical substitution or shift ciphers, Bacon’s Cipher focuses on concealment rather than encryption. The letters are encoded in a binary-like system, often hidden in another medium, making it a true steganographic cipher.